Personal
Unix
Programming
Networking
Documents
Reporting
Weblog
CityRail
BOM pictures
Other projects
Contact me
Basic Cisco Router SecurityThis document describes some basic security tips for Cisco routers. The tips are based on my experiences regarding routers during the time I was employed by Philips Communication and Processing Services, Origin IT and Atos Origin. These tips are basic tips to harden your network devices, but they are not the ultimate set of things to do. Keeping in mind how an IP network works and keeping your skills up to date with general networking- and security-mailing-lists is a must. Network layoutFor this document we have the following layout of the network: 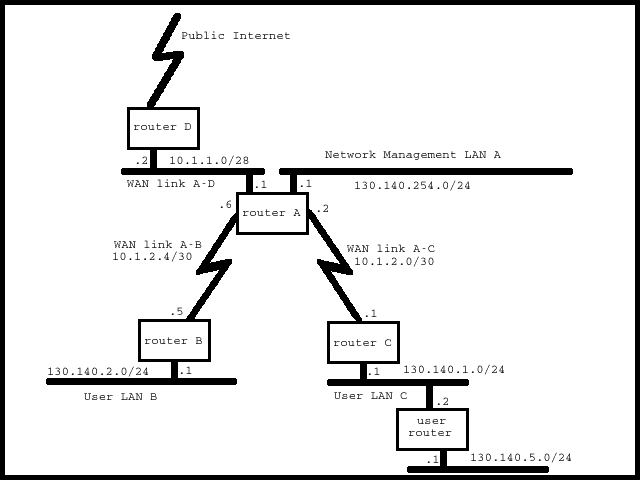
The following assumptions regarding network design are made:
Initial router configurationThere are a couple of things which are assumed to have happened:
Access securityThis part describes security to access the router via normal telnet. Authentication is done via TACACS+. The router should use it for both login- and enable-authentication. If no connection could be made with the authentication server it should fall back on the enable password. router-A(config)#aaa new-model router-A(config)#aaa authentication login default tacacs+ enable router-A(config)#aaa authentication enable default tacacs+ enable router-A(config)#tacacs-server host <ip address of TACACS+ server> router-A(config)#ip tacacs source-interface loopback0 Now an enable password should be defined. Cisco routers have three types of password-encryptions:
router-A(config)#service password-encryption router-A(config)#enable secret <password> Only TCP connections coming from the network management LAN are allowed to access the routers. router-A(config)#no access-list 1 router-A(config)#access-list 1 permit <subnet address of network management LAN> <subnet mask> Next it's finally time to enable the possibilities to login. There will no passwords specified on the lines because that's configured with the aaa statements. A 30-minute time-out shall be standard on all console and virtual terminal lines. router-A(config)#line console 0 router-A(config-line)#exec-timeout 30 0 router-A(config-line)#line aux 0 router-A(config-line)#no exec router-A(config-line)#transport input all router-A(config-line)#line vty 0 4 router-A(config-line)#access-list 1 in router-A(config-line)#exec-timeout 30 0 In the past, it was possible to access the router via the chargen or echo ports. These services are not needed and should be disabled: router-A(config)#no service udp-small-servers router-A(config)#no service tcp-small-servers SNMP securitySNMP is used to retrieve data from remote machines. This should only be allowed by machines on the network management LAN. If you want to allow non-network management hosts to have SNMP access to a router, put them in a different access-list and give them a uniq community-string. router-A(config)#no access-list 3 router-A(config)#access-list 3 permit <subnet address of network management LAN> <subnet mask> router-A(config)#no access-list 4 router-A(config)#access-list 4 deny any Let the router send its SNMP information to the SNMP server, which is on the network management LAN. If there is an unauthorized attempt to access the router via SNMP, let it send a warning to the SNMP server. Limit the machines which can perform SNMP queries to the machines on the network management LAN. Also disable the possibility to do a system shutdown via SNMP. router-A(config)#snmp-server community <community-string> RW 3 router-A(config)#snmp-server community <community-string> RO 4 router-A(config)#snmp-server host <ip address of SNMP server> <community-string> router-A(config)#snmp-server trap-source loopback0 router-A(config)#snmp-server enable traps snmp authentication router-A(config)#no snmp-server system-shutdown router-A(config)#snmp-server tftp-server-list 3 Routing Process securityThe routing-process is the most part of your network: If it is screwed up, your network doesn't function. Also, it gives a lot of information away is people have access to the routing-tables. If a routing-neighbour gets lost, it should be logged in the syslog: router-A(config)#router eigrp 12 router-A(config-router)#eigrp log-neighbour-changes All interfaces which are not connected to another router managed by you should be turned off for routing. router-A(config)#router eigrp 12 router-A(config-router)#passive-interface loopback0 router-A(config-router)#passive-interface ethernet0 Also, don't accept any routing information from routers not belonging to you. If you want to route to other routers on the user LANs, managed by you or not, use static routes which points to that router and let a default gateway point from them to your router. router-C(config)#ip route 130.140.5.0 255.255.255.0 130.140.1.2 router-C(config)#router eigrp 12 router-C(config-router)#redistribute static user-router(config)#ip route 0.0.0.0 255.255.255.0 130.140.1.1 Logging securityThe logging done by the routers can be send to a central host. If you enable this, make sure the syslog-deamom op that host allows syslog-messages from remote machines. router-A(config)#logging buffered router-A(config)#logging console debugging router-A(config)#logging trap informational router-A(config)#logging source-interface loopback0 router-A(config)#logging <ip address of syslog server> NTP securityKnowledge of the time with regarding to debugging, general logging and analyzing of problems is very important. Therefor all routers should have their time to a single source and accept no time information from any other source. It is also possible to configure routers to act as NTP servers for either other routers or to hosts on the user LAN. router-A(config)#no access-list 5 router-A(config)#access-list 5 permit <ip address of NTP server> router-A(config)#no access-list 6 router-A(config)#access-list 6 deny all router-A(config)#ntp access-group peer 5 router-A(config)#ntp access-group serve 6 router-A(config)#ntp source loopback 0 router-A(config)#ntp server <ip address of NTP server> User LAN Interface securityThe user LAN interfaces is the place where the traffic goes and comes from the users. And thus the place which will receive bogus and illegal packets first. There are a couple of things things to take care of:
|
||||||||||||||||||||||||||||